Lethbridge College takes Cyber Security very seriously. We believe it is important to ensure that the College community has access to helpful and relevant information to help keep us all safer from the constant deluge of Cyber Security, personal privacy and financial threats. This site is intended to provide tips, news items and communicate cyber security information.
Cyber Security and Acceptable Usage Policies
Cyber Security Tips
Lethbridge College Information Technology Services has compiled some Cyber Security Tips and best practices to help you navigate the digital world.
Social engineering is the technique of manipulating people in order to elicit cooperation for the purposes of compromising information technology systems or data.
Phishing:
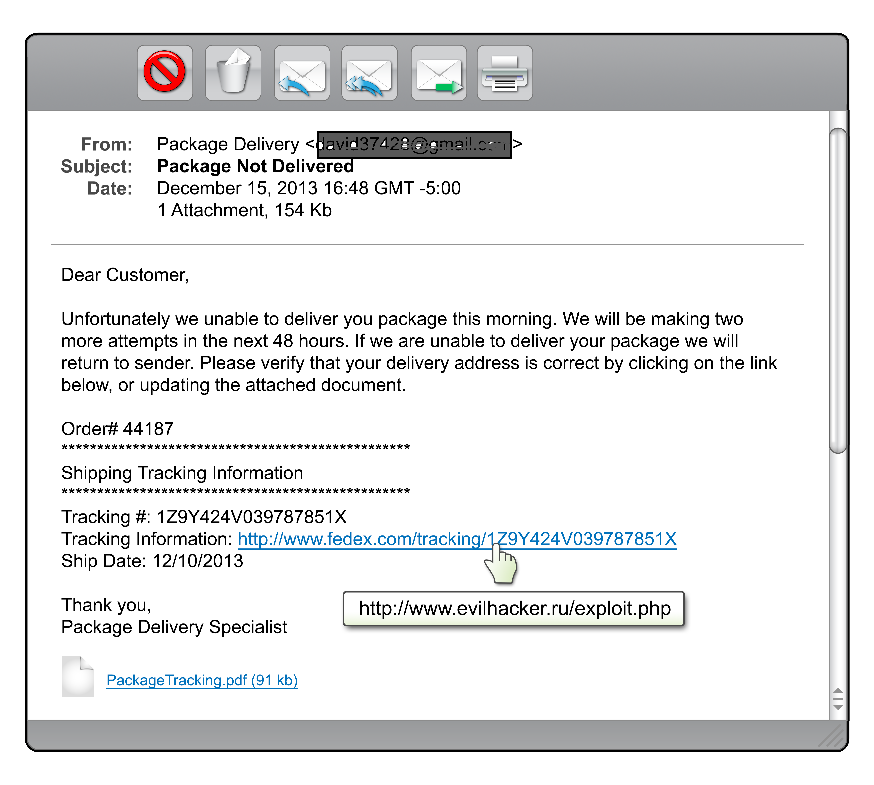
Phishing attacks use 'spoofed' emails that "appears" to be from a legitimate company. The e-mail usually contains a link to a web-site and asks you to verify your account information or supply personal identity data. While the link appears to be a legitimate site, it actually sends you to a forged website that looks like the real thing. If you log into the site, your credentials will be collected by the criminals.
Vishing:
Vishing is the criminal practice of using social engineering over the telephone system, most often using features facilitated by Voice over IP (VoIP), to gain access to private personal and financial information from the public for the purpose of financial reward. The term is a combination of "voice" and phishing. Vishing is very hard for legal authorities to monitor or trace. To protect yourself, you are advised to be highly suspicious when receiving messages directing you to call and provide credit card or bank numbers. When in doubt, calling a company's telephone number listed on the billing statement or other official source is recommended instead of calling numbers from messages of dubious authenticity.
Smishing:
Smishing occurs when a fraudster sends you a text message asking you to provide sensitive, personal, and/or financial information via a web link and false website, or a telephone number. The most common examples of SmiShing occur when fraudsters send text messages, posing as your financial institution, that threaten dire consequence if you don't respond immediately. The message may direct you to a toll-free number or website that looks just like a legitimate institution’s number, but in fact it is not. Once you have called the number or clicked on the email link, you may be asked to “verify” sensitive information such as credit card data, banking information and pass code, etc.
Email attachments:
This is a scam everyone should be familiar with.
You receive an email with a reasonable sounding subject line instructing the user that their is an important file attached to the email or they should "Confirm their account details" by clicking on a link.
When the user downloads or opens the attachment, the malicious code infects the user with malware.
- Don't open unsolicited or unexpected attachments.
- If you don’t recognize the sender of an attachment as legitimate, delete it.
- Legitimate email can always be resent
Credentials are information that is used to identify you and give access to web sites such as on-line banking, facebook, or email or enable you to logon to computers, tablets or even your phone.
Password complexity
- Use strong passwords that can't be easily guessed and protect them from disclosure
- Do not share passwords and do not write them down.
- Characteristics of strong passwords:
- Use a mix of upper and lower case letters, numbers, and symbols. (This adds more characters that need to be tried and significantly increases the time it takes to guess a password.)
- Minimum 12 characters long (Longer passwords are harder to brute force, which is a technique hackers use to try and guess all possible passwords using a password list.)
- Hard to guess (e.g. don't use personal information like user name, names of family members, places, pets, birthdays etc.)
- Easy to remember (So you don't have to write them down.)
- Do not re-use the same password when required to change your password.
- A password generation site can help you create new passwords. (https://www.random.org/passwords/)
- Using a password manager can help so you don't need to remember a complex and unique password for every site you authenticate to.
- Joining two or more known passwords can make a good strong password which will be easy to remember.
Example.
Password 1: H@ppy-41
Password 2: G0 Fl@m3$
Strong password: H@ppy-41G0 Fl@m3$
(17 character password which is relatively easy to remember)
Multi-factor authentication
Multi-factor authentication uses multiple means of authenticating your identity and is much more difficult for hackers/scammers to circumvent. If possible, take advantage of multi-factor authentication for your most private/sensitive data.
Examples of multi-factor authentication are any combination of the following:
- Something you know. (Like passwords)
- Something you have (Like a bank card or cellular phone)
- A unique characteristic (fingerprints)
- Geographic location or time of day. (Authorizing activity during work hours only)
Social media
Social media websites are a way for people to connect and share information with each other, and include blogs, wikis, and forums such as Facebook, Twitter, LinkedIn, Google+ and YouTube. However, these websites can pose a threat to users whom innocently share personal or sensitive information online.
Social media may present the following threats:
- Viruses: Cyber criminals can embed malware in a social media websites or third-party applications. Infected users can then spread the malware by unknowingly sharing malicious links and files.
- Third-party Applications: Third-party applications available on social media platforms, such as online games, may be used to access your personal profile information without the your consent. Even if the application is not malicious, the information gathered could be used for detrimental purposes,such as sending spam e-mails, accessing contacts without permission or criminal activity.
- Compromise of College Accounts: Cyber criminals use methods such as social engineering to take control of accounts which may lead to the breach of sensitive or critical college information assets.
- Identity Theft: Cyber criminals may access personal information about you which then enables them to assume your identity or collect passwords which can then compromise the security of your other online applications or services.
- Reconnaissance: Cyber criminals can gather information about you or your co-workers to craft socially engineered or spear phishing e-mails allowing for successful delivery of malware that can compromise the college.
- Data Misuse: There is a risk in using social media for college business. Posting too much information or information that has not been approved for public release can result in financial loss, reputation loss or even assist cyber criminals in a cyber attack against the college.
Setting alerts:
If possible, set alerts on sensitive web-sites such as banking/credit card, social media sites, email accounts and online utility accounts.
Create alerts:
- Whenever your account logs in to your banking and credit card accounts.
- Whenever large transactions are processed on banking or credit card accounts.
- Whenever your account is accessed or transactions are made from areas outside your geographic region.
- When your account details are changed on any site.
- When your password changes on any site.
It's paramount that the devices we use for day to day computing be kept as secure as possible. Some of the best practices for doing so are as follows.
Device Security
Operating System Updates
Ensure that your computers, mobile phones, home routers and internet connected devices such as Smart appliances have auto-update capabilities enabled. Cyber criminals and security researchers are constantly finding new vulnerabilities in software that vendors must patch. Keeping on top of these updates keeps you safe from these types of direct exploits.
Anti-Virus/ Anti-Malware
Install and maintain software that actively detects and stops viruses and other types of exploits from running on your computers and mobile devices.
Firewalls
A computer firewall is software that controls the incoming and outgoing network traffic based on rules. Ensure you have a firewall that monitors both incoming and outgoing connections to your computer. Windows 7, 8, 8.1 and 10 have built in firewalls but they are fairly permissive by default.
Device Encryption
Encryption is a process that turns the information stored on your device into unintelligible text characters that cannot be deciphered and read without the decryption key. An encrypted device will not convert its encrypted information back into plaintext unless the user provides the correct password.
However, encryption is not the same as password protection. Passwords can be broken or bypassed, and hard drives can be stolen. If the hard drive of a compromised device is unencrypted, the information stored on it can be read by those with less than honourable intent. Encryption takes your security one step further by actually converting the information stored on your hard drive into unintelligible text.
- One laptop is stolen every 53 seconds.
- 70 million smartphones are lost each year, with only 7 percent recovered.
- 80 percent of the cost of a lost laptop is from data breach.
- 52 percent of devices are stolen from the office/workplace, and 24 percent from conferences.
Encryption ensures that if someone does steal your device, the information on your computer cannot be read unless the thief can log onto your device. As a member of the Lethbridge College community, your computing devices may contain sensitive information about the College, its students, its employees, its intellectual property or yourself. This data is a target for hackers and identity thieves, and passwords are not enough to keep it safe. Encryption ensures that if someone takes your device, they cannot read the information on it.
What types of devices need to be encrypted? Any mobile or portable personal, external, or College-owned device that contains College information must be encrypted. This includes laptops, mobile phones, tablets, and USB flash drives. Encrypting these devices is in accordance with standards developed by Lethbridge College Information Technology Services.
Who needs to encrypt?
The short answer: everyone. Encryption protects your files, photos, accounts, and information. If you have anything on your device intended for your eyes only, then encrypt it.
Employees of Lethbridge College have an extra responsibility to encrypt because their devices may contain confidential College information. By encrypting your device, you are ensuring that you are doing all you can to protect the College and its people.
What sort of information can encryption protect?
Encryption protects any information stored on your device and/or your device’s hard drive, and it is especially important for protecting sensitive information.
According to the College’s Information Access and Privacy Office, sensitive or confidential information is defined as all information that has been collected or compiled in the conduct of operating the programs and services of the College, and may include:
- personal information about an individual as defined in the Alberta Freedom of Information and Protection of Privacy Act (including personal financial, social insurance, work history, and contact information)
- health information as defined in the Alberta Health Information Act
- confidential business information of third parties
- confidential information collected or compiled in the process of hiring or evaluating employees of the College
- information collected or compiled in the process of law enforcement investigations
- advice, proposals or recommendations, consultations or deliberations of the governing and administrative authorities of the College
- information, the disclosure of which would harm the economic interests of the College
- any information to which legal privilege, including client-solicitor privilege, may apply
Below are helpful links showing how to enable encryption on common devices.
Protect Mobile Devices and removable media.
- Don't keep sensitive information or your only copy of critical information on mobile devices (laptops, phones, tablets, etc.) or removable media (memory sticks, DVDs, etc.) unless they are properly protected.
- Don't install or download unknown or unsolicited programs on your computer. These can install viruses on your computer or open a "back door" giving hackers access to your computer.
- Make backup copies of files or data you are not willing to lose -- and store the copies very securely, preferably in multiple locations.
- Ensure programs installed on your device(s) are configured to automatically receive updates and restart your computer when prompted to in order to install software updates.
- Regular reboots of Windows devices helps maintain the health of the device as some maintenance processes only run on user logon or boot up.
- Turn Bluetooth off and not accept files over Bluetooth without knowing what and who it is from. Malicious software, like viruses, can be spread via Bluetooth.
Malware is any software, program or code that performs unwanted and unauthorized activity on a computing device.
Malware can spy on your activities, corrupt files, spread to other devices, send email spam to other users, cause your device to participate in attacks on public web services, attempt to hold your private data for ransom and use the computing resources on your device for unlawful purposes.
Many people have the misconception that malware is a problem only for Windows computers. While Windows is widely used, and thus a big target, malware can infect any computing device, including smartphones and tablets. Incidences of malicious software infecting mobile devices is steadily growing.
Here are some steps to help prevent Malware from infecting your devices.
- Install anti-virus software from trusted vendors on all the devices that you want to protect.
- Install and maintain anti-exploit software such as Malwarebytes anti-exploit. This software examines behavior of applications and decides if the behavior is typical for Malware.
- Make sure your operating systems and applications are enabled to automatically install security updates.
- Ensure your computer is rebooted regularly.
- Be alert for Phishing scams that entice you into installing malware onto your device.
- Install software only from trusted sources.
Remember that everyone is a target, including you.
How do you protect your sensitive information when using the Internet and email?
- Don't log in to web sites or online applications unless the login page is secure.
Look for https (not http) in the URL to indicate that there is a secure connection or depending on the browser, the lock icon ![]() and/or the word secure somewhere in the address bar. Be careful about what you do over wireless internet connections. Information and passwords sent via standard, un-encrypted wireless are especially easy for hackers to intercept (most public access wireless is un-encrypted)
and/or the word secure somewhere in the address bar. Be careful about what you do over wireless internet connections. Information and passwords sent via standard, un-encrypted wireless are especially easy for hackers to intercept (most public access wireless is un-encrypted)
- Don't enter personal or sensitive information online unless you are using a trusted, secure web page.
- Set laptops and mobile devices to “ask” before joining networks so you don’t accidentally connect to unsecured wireless networks
- Don't send sensitive data via un-encrypted email.
- File-sharing software places your computer at risk of infection via malicious files and attackers. Also, if you share sensitive or copyrighted files, you can be disconnected from the campus network, and face legal consequences.
- If you are unsure about a web-site link, hold your mouse cursor over the link. The URL (Web site which the link points to) should appear in the bottom status bar of most modern browsers) If it's not the site you expected, do not click the link.
Encryption is the conversion of data into a form, called a ciphertext, that cannot be easily understood by unauthorized people.
- If a web-site has been compromised, you can be infected if you click a link to a video or other media and the web site asks you to update the media player with a new version. The newer software version may be a virus or trojan..

- In recent years, even prominent web-sites and businesses have been compromised. Keeping abreast of the news can help you avoid becoming a victim.
Protecting personal information
The following tips offer some general advice to help individuals better protect their personal information.
Provided courtesy of the government of Canada.
https://www.priv.gc.ca/en/privacy-topics/your-privacy-rights/02_05_d_64_tips/
1. Think twice
Whether online or face-to-face, you are asked to provide personal data at every turn. Don’t turn it over blindly. Think about why the information is required, how it may be used and by whom. Remember, the Net never forgets. Once information is out there, it’s very difficult to get back. Think of the impact certain comments or images could have on your reputation or the reputation of others. Respect other people’s privacy.
2. Ask questions
Get in the habit of reading privacy policies associated with the websites and apps you use. Companies should be able to answer any questions you have about how your information will be used and protected. If they can’t, or you don’t like what you hear, this should raise red flags.
3. Speak up
If you have concerns about the personal information handling practices of an organization, your first step should be to bring it to their attention. Most organizations are sensitive to consumer concerns about privacy. In many cases, a concern you have about how your personal information has been handled by an organization can be quickly and effectively addressed if you raise it directly with them. Positive change to the general policies or practices of an organization are more likely when people speak up.
4. Just say no
Consider subscribing to the National Do Not Call List to avoid telemarketers. Check off the “no thanks” box on forms when asked to provide personal information or leave a brief note stating your refusal to be contacted. You can also get your name removed from many mailing and telephone lists by writing to the Canadian Marketing Association. Report email solicitations that are fraudulent or misleading or that you did not consent to receiving. It may be spam and the sender may be breaking the law.
5. Safeguard your SIN
Your Social Insurance Number is important to privacy protection because it can open the door to your personal information and put you at risk of fraud and identity theft. Your SIN is confidential and should only be collected and used for income reporting purposes. Avoid sharing it with private-sector organizations or individuals such as landlords.
6. Get to know privacy settings
Mobile devices, browsers, sites/apps and other web-enabled items such as video games and cameras often have adjustable privacy settings. For devices, this may include the ability to control everything from location tracking to screen locks. For browsers, users can often control things like cookies and pop-ups, while apps and websites such as social media sites generally allow users to control what personal information others can see about them. Be sure to review and adjust privacy settings regularly and never rely on default settings.
7. Discard with discretion
Make sure data stored on devices you no longer use is properly purged before recycling or discarding. When doing business with a particular company, be cognizant of its personal information retention periods and disposal practices. Ask questions if you are uncertain.
8. Know your rights
Read up on the basics of Canada’s federal privacy laws: the Privacy Act, which applies to the personal information handling practices of federal government institutions, and the Personal Information Protection and Electronic Documents Act (PIPEDA), Canada’s federal private sector privacy law. Remember, you have the right to access and correct your personal information.
Further information about how to protect your privacy is available on the website of the Office of the Privacy Commissioner of Canada. Provincial and territorial privacy oversight offices also offer privacy information on their websites.
Securing Your Home Network
Home networks are more complex than ever before and we are connecting more devices to them and doing more things with them.
Here are some steps for creating a more secure home network.
Malicious exploits now target home routers. These exploits change the DNS settings on the home router and allow interception of all traffic leaving your home network. Users may then be redirected to fake banking sites, allowing user accounts to be compromised. Check with your routers manufacturer web-site to see if your router is vulnerable.
Many home networks use a wireless network (also known as Wi-Fi). This technology allows you to connect many of your devices to the Internet. Things such as laptops, tablets, gaming consoles, televisions and even your refrigerator. To do this, WiFi uses a wireless access point. This is a physical device connected to your Internet router and acts like a radio transceiver that sends out a wireless signal for your devices to connect to. Once connected, devices can then "talk" to other connected devices on your home network and the Internet. Use the following steps to secure your wireless access point.
- Most wireless access points have a default administrator login and password which are well-known and likely posted on the Internet. So be sure to change the default administrator login and password to something known only to you.
- Do not allow/enable remote management to the router. This is an attractive target to hackers and usually a fairly easy compromise to perform.
- Don’t use the default IP ranges. Most routers perform DHCP (Dynamic Host Configuration Protocol). This process allocates IP addresses to the machines on your home network. (Think of this as akin to having an mailing address for your computer. If an attacker can guess the addresses in use they can join your network incognito.)
- Change the name of your wireless network or SSID. This is the name displayed if you search for local wireless networks. Changing your network name to something unique allows you to easily identify it.
- Do not rely on setting your network SSID to hidden, most wireless detection tools can easily sniff out hidden networks.
- Ensure that only devices and people you know and trust can connect to your wireless network, and that those connections are encrypted by enabling strong security on your wireless access point. Enabling WPA2 requires a password for people and devices to connect to your home network and such connections are encrypted. Do not use older security methods such as WEP, or no security at all (which is called an open network).
- Disable WPS (Wireless protected setup). This service is convenient for users joining the network, but is also easy for hackers to exploit.
- Use a strong unique password for users and devices to connect to the network. Do not use the Administrator password!
- Secure Guest networks with a different password.
- Identify all the devices on your home network and be sure you know what they are. Most access points allow you to disconnect or block suspect devices.
- Keep all your devices software/Operating System, including the access point and router, up to date. Enable any auto-updating features on these devices.
- Use a utility such as routercheck (www.routercheck.com) to see if your router has been compromised or is vulnerable.
- Ensure you log out of any sessions after you configure the router.
Reporting computer security incidents
...because sometimes it seems like you can do everything right and things still happen.
- Report any suspected compromise (hacking, unauthorized access, etc.) of computing systems or data to your supervisor and the ITS helpdesk
- Also report lost or missing College computing equipment to the ITS helpdesk (and to the local authorities if the incident occurred away from campus).
- See Reporting A Security Incident for additional information
I've been hacked! What now?
Sooner or later it is likely everyone will suffer data loss or be subject to a threat to their identity via a phishing scam.
Thus it is important to know what to do if such an event arises.
Of critical import is speed. The faster you react the less damage may occur.
Here are some indicators your computer has been compromised.
- Your anti-virus program has triggered an alert that your computer is infected, particularly if it says that it was unable to remove or quarantine the affected files.
- Your browser’s homepage has unexpectedly changed or your browser is taking you to websites that you did not want to go to.
- There are new accounts on your computer that you did not create.
- There are new programs running that you did not install.
- Your computer is continually crashing or running very slow.
- A program on your computer requests your authorization to make changes to your system, although you’re not actively installing or updating any of your applications.
- Your firewall alerts you that a program you do not recognize is requesting permission to access the internet.
If any of these conditions occur, please report the issue to the help desk immediately. If you believe there is a threat to network resources or files on your computer, disconnect the device from the network or power it off.
Identity Theft
Identity theft is the act of impersonating another, by means of using the person's information without permission including but not limited to the following:
- Name
- Address
- Phone number
- Date of birth
- Social Insurance number
- Mother's maiden name
- Bank account information
- Credit card information
- Driver's license numbers
- Signature
- Passwords
Identity theft is a serious fraud and criminal activity that causes severe damages to the victim.
Thieves often use the victim's personal information to open bank accounts, apply for credit cards, apply for auto/student loans or mortgage, rent apartments, commit crime, etc all in the victim's name without their knowledge. The victim can also be arrested due to frauds done by the impersonator under the victim's name.
Symptoms
- You see unauthorized charges on your credit card or bank accounts.
- You are contacted by a collection agency regarding a debt you did not incur.
- You receive bills from a credit account you did not open.
- Bank and credit billing statements don't arrive on time.
- You are turned down for a auto/student loan, mortgage, credit card,or other form of credit due to unauthorized debts on your credit report.
- Your credit report shows accounts you did not authorize.
Protecting yourself from identity theft
- Review your credit card statements and bank statements for discrepancies.
- Order and review your credit report from the credit reporting bureaus at least once a year.
- Shred all credit card statements, bank statements, pre-approved credit card offers, and any paper that has your personal information.
- Never leave or throw away credit card receipts in public.
- Do not respond to pre-approved credit card, auto loan or mortage offers from unknown sources.
- Never give personal information over the phone such as social security number or financial information unless you initiated the phone call.
- Do not carry your SIN card with you; leave it in a secure place.
- Do not post personal information on your personal website or on the internet.
- Change passwords frequently and follow good password practices.
- Download a free scam detection tool like Scam Detector
What to do if you're a victim of identity theft
It is important to take action right away to minimize future damage.
- Fill out the ID Theft information from Service Alberta
- Call creditors to let them know the accounts may have been opened fraudulently. If your existing accounts have been accessed, get new cards and account numbers.
- File a police report and send a copy to your creditors. This report helps document the crime.
- Report the theft to The Canadian Identity Theft Support Centre.
- Keep copies of all the information you collect for future reference.
- Reference the RCMP scams and fraud website. http://www.rcmp-grc.gc.ca/scams-fraudes/index-eng.htm
Criminals use scams and fraud to obtain money from individuals and businesses through many different means.
These include, but are not limited to: identity theft, telemarketing scams, door-to-door scams, online scams, business scams, mail scams, social media scams, and romance scams.
While it may not happen to you, criminals are using increasingly sophisticated tactics, such as Artificial Intelligence, to target vulnerable people.
Knowing how to spot these scams may save you, a friend, or a relative from falling victim to cyber criminals.
Tips
- Be careful about providing personal information, especially banking or credit card details. Only provide this information when you are certain a company is legitimate.
- Monitor your financial accounts. Report any fraudulent charges to your financial institution immediately.
- If in doubt, ask for written information, a call back number, references, or time to think over an offer.
- Ask the advice of someone you trust.
- Some scammers (Typically romance scams) take great efforts and time to set up their target. They may not ask a potential victim for anything initially, and instead build up trust and emotional connection between scammer and victim. Once that trust is sufficiently established, the scammer will then ask for money, usually because of some emergency. Unfortunately, this is very effective and individuals have been scammed out of life savings in this way.
Warning Signs
- A deal sounds too good to be true.
- You are asked to provide financial information.
- You are asked to send cash money, money orders, bitcoins or gift cards.
- A person claims to hold a position of some authority (government official, tax officer, banking officer, etc.) and threatens to use that authority if you do not comply.
- A sense of urgency is created to pressure you into acting quickly.
- The person asks you many personal questions and attempts to be overly friendly
What to do if you become a victim
- Step 1: Gather all information about the fraud (e.g. documents, receipts, emails, text messages)
- Step 2: Report the incident to your local police or RCMP. Keep a log of all your calls
- Step 3: Contact the Canadian Anti-Fraud Centre
- Step 4: Report the incident to the financial institution where the money was sent
- Step 5: Report to any relevant websites if the fraud took place online
- Step 6: Report to credit bureaus to place flags on all accounts (e.g. Equifax and TransUnion)
- Step 7: Inform your family and friends to help them avoid a similar scam.